Ten tools to optimize CSS
Optimize your CSS (template)
I'm going to make an account very simple math: you have a website or blog, you want your blog / web fulfill a function, whatever this I assure you that you need visits , muuch views (come on, is what we all want) from which the highest percentage of visits to a page? RIGHT .. "Seekers" .. So we must be liked google to put us in these top positions that we all desire .. To do this we need to follow a series of tasks to googlebot (robot google) indexing us in his wonderful form and give us a good place in that ranking ..
Of all the tasks to be accomplished, there are many (notice that we do not get that position in the google search with a single task to follow but with the whole lot) Today I hablere on how to optimize a template .. And explain why ..
to Googlebot likes and looks favorably pages muyy lightweight, easy to carry for the convenience of the visitor (remember also that not everyone has your wonderful connection ^ ^) between These include: The iframes, images, banners, videos, TEMPLATE (Very important is) the above package does or does not make your site load quickly or pessimistic about any form, is a fact and we must fight. . While the googlebot Caigamosle;)
acontinuación
What you teach, will be 10 very cute tools to reduce weight in "kb" in our template basically what these do is reduce unnecessary spaces and other settings to squeeze other minimum.
Clean CSS: Very easy to use simply paste the code or give you the url of it.
can set the desired level of compression (the offset to a greater understanding of reading is more difficult) and customize the compression settings. A report is printed line by line afterwards to show exactly what was changed.
Flumpcakes: same methodology, it is not practical, when generating optimized code have to copy and paste the new CSS manually.
An interesting feature is the backlink function that provides a URL that can score at any time to see the compressed state of the style sheet.
Icey CSS Compressor: Extremely fast, has the "problem" that does not generate the file, copy directly from the html it generates.
There are plenty of compression options can be set and handles color, measurements (units), rules and CSS properties. It also provides a useful tool for simultaneously combining and compressing the combination of three separate CSS files.
CSS Drive's CSS Compressor: has two modes, normal and advanced mode (which has a few options that can be set). You can delete the comments (strip comments option) or specify to strip comments above a certain character limit, so it retains comments are short. regular mode is perfect for those who are not very demanding - just choose between Light, Normal, and Super Compact compression and you're ready to rock.
Online CSS Optimizer : is another simple tool optimization. You have two ways to entreda in your CSS: either through the text box on the page or link directly to your style sheet. Sometimes you need to reverse pass compression, it can be done through CSS Unzip application on the site. (Useful in some cases)
Format CSS: FormatCSS allows you to paste the CSS code valid, correct and standardize the source code. There are several options available and the rules can be applied to achieve the kind of format you want - including an order of CSS in alphabetical order, of the capitalization of your code, and some options to deal with the styles.
Prettyprinter.de: CSS is not limited to - well formats PHP, Java, C + +, C, Perl and JavaScript, which is an excellent "one-stop-shop" for your formatting needs if you have to work with any of the other supported languages. There are a total of 13 different options can be established between them "Reducing the blanks," "Remove empty lines, and automatically after the addition of new lines of keys.
CSS validation Service: is very easy to use, just enter the URL of the style sheet and will show the status of your page, point out the errors, warnings and other issues.
Tabifier: is the multilingual web-tool specifically designed for the normalization of scripts in the source code. It supports HTML, CSS and C style It is a simple tool, excellent for quick formatting of scripts.
CSS Optimizer: Optimizer is a very simple, you have the option of linking to the URL of your style sheet, loading a CSS file, or directly by entering their styles. It is a simple tool that "plug-and-chu" no options, so the optimization procedure will remain the same.
best of the best;) for those webmasters or bloggers (aprendicez or veterans) If you want to test little by little with each one, perfect .. On the other side without intention of giving preference to one in particular (Why can not I use to be the best but the habit ^ ^).
Clean CSS is the commonly used .. Not would call for favorite because everyone helped me a lot, but rather the habit ^ ^
As I know very well that you are on that topic intereza magic of "positioning" favorite search engine .. Little by little I will be showing all measures and tasks to continue to go through the ranks in Google, yahoo or any other search engine ..
Friday, April 30, 2010
Wednesday, April 28, 2010
Wearelinguists.narod.ru
Elements of a template (BLOGGER) anti-hacker security
! Problems with your template?
Once again bringing material =)
This time I want to expose something that brought me MANY headaches! And is that the programming the hack the carding , so cool me and draws me .. But designer and blogger Buuf as such, say I'm learning! I hope to go far before dying hehe .. In my early
blogger much sealed me templates and components, until I could master a bit the question and now I want to show some of the basics for those who start with a blogger and never tire of making attempts ending in failure = (
I take the trouble to make a sample drawing so you can appreciate a bit more detail every part and section of this! We greatly regret the bad visual, but I did it on purpose, taking into account that the image weighs nothing and enhances the performance and optimal load of blog search engines ( Another issue that then speak ) and therefore on your machine!
below explains each of the sections with its own color as I am well aware that the image is very poor ..
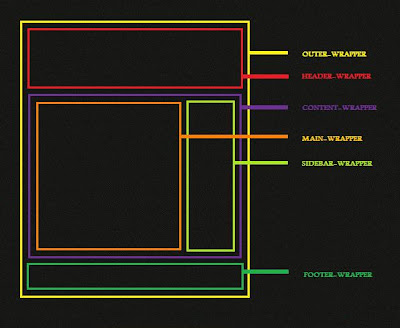
containers: outer - wrapper, header - wrapper, content - wrapper, main - wrapper, sidebar - wrapper, footer - wrapper.
For example I have considered just a sidebar but should be 2 in Blogger sidebar often called 1 - wrapper and sidebar 2 - wrapper.
The outer - wrapper is the main blog package, the largest, which defines the total width (which pereferencia should not exceed 960 pixels so as to avoid horizontal scrolls, even using the extension All in one of Firefox sidebar to cut horizontal space) and other parameters.
The header - wrapper is the one containing the header, our logo , Etc. Obviously the width of this and the other main elements contained in the outter - wrapper must be less than or equal to it, but there will be overflow errors (which we'll talk in another post), especially in Internet Explorer.
The content - wrapper is the container for content, I do not mean the container posts , but it encompasses a larger sidebar and posts . Like the header - its parameter wrapper wide (width ) should be less than or equal to the outer - wrapper.
The main - wrapper is the container for posts , here for example you can choose a background color for the entire field or margins over the limits of content - wrapper or paddings, etc.
The sidebar - wrapper is the container for sidebar , one in which are contained all our widgets and / or elements that have shaped incorporates its html code, javascript, images or similar. Here usually set (in) the style of the lists (eg for input or file, the blogroll or links, etc.).
The footer - wrapper lower container is one blog which publishes the theme credits, the hosting , licenses, authors, etc.
Now that you know the elements Blogger wrapper can begin to move CSS code in the correct sections and solve problems (such as sidebars to be the ground or move to the bottom of the blog to be seen Internet Explorer). PD
: If any of you a particular problem, leave your doubt gladly go up a manual in this regard ..
luck with your blogs and if you want a mutual bonding entice visitors to go, just ask! 
! Problems with your template?
Once again bringing material =)
This time I want to expose something that brought me MANY headaches! And is that the programming the hack the carding , so cool me and draws me .. But designer and blogger Buuf as such, say I'm learning! I hope to go far before dying hehe .. In my early
blogger much sealed me templates and components, until I could master a bit the question and now I want to show some of the basics for those who start with a blogger and never tire of making attempts ending in failure = (
I take the trouble to make a sample drawing so you can appreciate a bit more detail every part and section of this! We greatly regret the bad visual, but I did it on purpose, taking into account that the image weighs nothing and enhances the performance and optimal load of blog search engines ( Another issue that then speak ) and therefore on your machine!
below explains each of the sections with its own color as I am well aware that the image is very poor ..

containers: outer - wrapper, header - wrapper, content - wrapper, main - wrapper, sidebar - wrapper, footer - wrapper.
For example I have considered just a sidebar but should be 2 in Blogger sidebar often called 1 - wrapper and sidebar 2 - wrapper.
The outer - wrapper is the main blog package, the largest, which defines the total width (which pereferencia should not exceed 960 pixels so as to avoid horizontal scrolls, even using the extension All in one of Firefox sidebar to cut horizontal space) and other parameters.
The header - wrapper is the one containing the header, our logo , Etc. Obviously the width of this and the other main elements contained in the outter - wrapper must be less than or equal to it, but there will be overflow errors (which we'll talk in another post), especially in Internet Explorer.
The content - wrapper is the container for content, I do not mean the container posts , but it encompasses a larger sidebar and posts . Like the header - its parameter wrapper wide (width ) should be less than or equal to the outer - wrapper.
The main - wrapper is the container for posts , here for example you can choose a background color for the entire field or margins over the limits of content - wrapper or paddings, etc.
The sidebar - wrapper is the container for sidebar , one in which are contained all our widgets and / or elements that have shaped incorporates its html code, javascript, images or similar. Here usually set (in) the style of the lists (eg for input or file, the blogroll or links, etc.).
The footer - wrapper lower container is one blog which publishes the theme credits, the hosting , licenses, authors, etc.
Now that you know the elements Blogger wrapper can begin to move CSS code in the correct sections and solve problems (such as sidebars to be the ground or move to the bottom of the blog to be seen Internet Explorer). PD
: If any of you a particular problem, leave your doubt gladly go up a manual in this regard ..
luck with your blogs and if you want a mutual bonding entice visitors to go, just ask!
Monday, April 26, 2010
Go From Ssi To Ssd Age 21
on Blogger (Tutorial) hide under the Svchost.exe process By Jeshua
PROTECT YOUR BLOGGER
hacker Many have been attacked by hackers who are dedicated to throw down the floor all websites and blog that they get is that if something is abundant in this world is the defacing.
Therefore we must try even in the least to protect ourselves such attacks among the best known are the scam:
many receive multiple mailings in their requests to reset your password Google Gmail, Hotmail has a system in which they warn that it has been tried many times to enter your email address, other e-mail systems like Yahoo have their own methods to protect or warn of a possible hack attempt BUT for some reason Blogger has nothing to protect themselves from hacking an account (not surprisingly), all would be arming a security system manual with which to protect and support your blog from time to time.
Many have been victims of such scams computing to the point of leaving any blog KO (deleting all information or even stealing the full blog)
therefore the most effective way I think to guard against a hacker attack is
:
antihacker Blogger Tutorial:
1 .- Create an account ultra in Gmail
1.a. - The mail must be very rare and never, ever use it or give it to anyone.
2 .- Use a password so rare that you will not learn it by heart and keep it in a piece of paper, use something like this: 387LosCoMuniStasvaLenVergA756 , well ... not be as exaggerated, but try to have numbers at the beginning and end mixing uppercase and lowercase osea an alphanumeric code: D
2.a. - Never use a key that relates to you, all of your favorite food, the name of your pet, your middle name nothing, nothing in your date of birth or yours or that of any known, the worse your children or wife (of course never your wife), obviously do not use "garfield" statistically more recognized as the key used by women aged 15 to 25 years.
3 .- Go to Blogger: Dashboard / Settings / Permits, and send an invitation to your new account as if it were a guest over to your blog to post.
Open 3rd-mail your guest, ultra ghost in another browser and accepts the invitation.
4 .- In your normal user permissions to your guest ghost endow "Admin privileges."
5 .- Then go to Blogger in the other browser with your new account ghost and take off your normal user administrator privileges, this means that you will continue posting as usual but from now on you will as a guest.
5.a. - A visitor to your blog has limited actions, he can only edit your post, edit the post can never rest, and less able to access your blog design and setup where you can delete the blog entirely.
5.b. - This will be protected should they hackearte your normal user, the most that will happen that will erase your post (you will not care for that have supported), and you lose your Blogger profile usual, but after creating you're solving a different profile with same name as you lost.
6 .- Finally Take off your fake user options to see the profile, you do this within: Desktop / Edit Profile / Privacy / share my profi (take away the go) and then right there in safety / Privacy, put where it says: "Select the posts you want to show" and uncheck your blog, so no user will know that there will be a ghost total and absolute: D: D
6.a. - And now, if the latter, in your user ghost in: Settings / Comments, which says: "Email notification of comments" Always put your mail for you are notified when you get a new comment.
Annexes. 1 .- ghost With your new account you can login normally to your blog and edit things like design and configuration, obviously you should not ever because I will post this as an author. Annexes
1.a. - When you enter your user ghost never do it from Internet Explorer wareber, as the "Ie" have a dog's safety, the reason is that to be integrated into the operating system means that update would update the damn tooodo operating system, comes always from Opera, which is the most efficient browser with security in the world, I do not recommend Firefox security (although it is very respectable), only Opera which is known worldwide for their benefits at the level of security.
Final 1 .- and ready, this is exactly the same as the security that gives you Windows Vista or Linux where you can not do anything important, but you have administrator privileges which it has only one who has the key. Conclusion .-
For many reasons blogs in Wordpress are not very confident that say they depend on each server or hosting but Marthita say it is true that offers many advantages, but I prefer between the many disadvantages of a single Blogger "security", a Blogger Blog is practically "inhackeable" unless averiguen your password and if they do even after this tutorial is only "fault".
Enjoy it, hope you find it useful. 
PROTECT YOUR BLOGGER
hacker Many have been attacked by hackers who are dedicated to throw down the floor all websites and blog that they get is that if something is abundant in this world is the defacing.
Therefore we must try even in the least to protect ourselves such attacks among the best known are the scam:
many receive multiple mailings in their requests to reset your password Google Gmail, Hotmail has a system in which they warn that it has been tried many times to enter your email address, other e-mail systems like Yahoo have their own methods to protect or warn of a possible hack attempt BUT for some reason Blogger has nothing to protect themselves from hacking an account (not surprisingly), all would be arming a security system manual with which to protect and support your blog from time to time.
Many have been victims of such scams computing to the point of leaving any blog KO (deleting all information or even stealing the full blog)
therefore the most effective way I think to guard against a hacker attack is
:
antihacker Blogger Tutorial:
1 .- Create an account ultra in Gmail
1.a. - The mail must be very rare and never, ever use it or give it to anyone.
2 .- Use a password so rare that you will not learn it by heart and keep it in a piece of paper, use something like this: 387LosCoMuniStasvaLenVergA756 , well ... not be as exaggerated, but try to have numbers at the beginning and end mixing uppercase and lowercase osea an alphanumeric code: D
2.a. - Never use a key that relates to you, all of your favorite food, the name of your pet, your middle name nothing, nothing in your date of birth or yours or that of any known, the worse your children or wife (of course never your wife), obviously do not use "garfield" statistically more recognized as the key used by women aged 15 to 25 years.
3 .- Go to Blogger: Dashboard / Settings / Permits, and send an invitation to your new account as if it were a guest over to your blog to post.
Open 3rd-mail your guest, ultra ghost in another browser and accepts the invitation.
4 .- In your normal user permissions to your guest ghost endow "Admin privileges."
5 .- Then go to Blogger in the other browser with your new account ghost and take off your normal user administrator privileges, this means that you will continue posting as usual but from now on you will as a guest.
5.a. - A visitor to your blog has limited actions, he can only edit your post, edit the post can never rest, and less able to access your blog design and setup where you can delete the blog entirely.
5.b. - This will be protected should they hackearte your normal user, the most that will happen that will erase your post (you will not care for that have supported), and you lose your Blogger profile usual, but after creating you're solving a different profile with same name as you lost.
6 .- Finally Take off your fake user options to see the profile, you do this within: Desktop / Edit Profile / Privacy / share my profi (take away the go) and then right there in safety / Privacy, put where it says: "Select the posts you want to show" and uncheck your blog, so no user will know that there will be a ghost total and absolute: D: D
6.a. - And now, if the latter, in your user ghost in: Settings / Comments, which says: "Email notification of comments" Always put your mail for you are notified when you get a new comment.
Annexes. 1 .- ghost With your new account you can login normally to your blog and edit things like design and configuration, obviously you should not ever because I will post this as an author. Annexes
1.a. - When you enter your user ghost never do it from Internet Explorer wareber, as the "Ie" have a dog's safety, the reason is that to be integrated into the operating system means that update would update the damn tooodo operating system, comes always from Opera, which is the most efficient browser with security in the world, I do not recommend Firefox security (although it is very respectable), only Opera which is known worldwide for their benefits at the level of security.
Final 1 .- and ready, this is exactly the same as the security that gives you Windows Vista or Linux where you can not do anything important, but you have administrator privileges which it has only one who has the key. Conclusion .-
For many reasons blogs in Wordpress are not very confident that say they depend on each server or hosting but Marthita say it is true that offers many advantages, but I prefer between the many disadvantages of a single Blogger "security", a Blogger Blog is practically "inhackeable" unless averiguen your password and if they do even after this tutorial is only "fault".
Enjoy it, hope you find it useful.
Thursday, April 22, 2010
Star Trac Treadmill Belt Wax Powder
Find out if your Web GoogleBot step. By virtux
The future and the spammer
Not many know but one thing that gives more money in this country but are hard to believe email marketing campaigns .. Income earned are above normal salary of any player in the first division.
First of all I would like to give you a brief definition of what is email marketing .. under concepts sought by the network:
Email marketing: is a form of direct marketing that uses email as a means of advertising or communication of messages to a specific audience.
Email marketing: are the actions and strategies for marketing through the Internet, which are carried out using the e-mail messages.
Email marketing: could be defined as the use of email for commercial purposes so that by sending emails to your customers or prospects can keep you informed about your products or services and initiate a dialogue in two directions (business - customer or prospect and vice versa).
guess I'm clear, this is an issue that attracts me MUUCHOO, however this post is not to speak especially of email marketing .. And publishes a new article on this subject. The root of this post is to let them see a bit where you get that causes brings the practice of email marketing when he became SPAM (junk mail) ..
Well here I bring a couple of news .. (Nothing new) but worth seeing .. BY OUR RETINA
I was looking for information on spam, programs, laws, etc etc. ..
And I have found especially with these 2 that UFF .. Sometimes I get to find the article and read it again and again and again! hehe .. Until this I have said baah share it with someone and then have the ad in house = P hehe ..
Here I bring you:
Sentenced to nine years in prison on eight "spammer" world's most prolific
Jeremy Jaynes, 30, has become the first spammer to be convicted U.S. to send up to 10 million unsolicited messages ("spam") that is pornographic and fake products to day. Jaynes, known as the eighth "spammer" world's busiest, has been sentenced to nine years in prison.
confesses A retired spammer tactics of the dark world of garbage
"I know I'm going to hell" is the owner of a great interview with ComputerWorld Australia where a spammer "retired" (not in the sense bladerunneriano , but in the economic) and some of their tactics and how the daily lives of those who send spam from the dark side. These are some of the highlights of the interview, complete worth reading:
Ed is a retired spammer made a considerable fortune sending promotional mailings pills, porn and casinos. At its peak earning between 10,000 and 15,000 dollars a week (...) He started his business when he was expelled from school at 17, until he retired at 22. "Yes, I know I'm going to hell. But I'm not bad guy, really. I'm basically everything that people hate to Internet. "
Among their techniques were sending spam to recovering gambling addicts by encouraging them to visit sites and casino games. He used the addresses of people I knew who bought antianxiety medication or antidepressants and pharmaceutical spam sent them (...) He spent ten hours a day, seven days a week studying how to send more spam and security filters overcome. "The best was sending spam, the more money earned." (...)
If someone who received the messages bought something, Ed received a percentage. In pharmaceuticals, about 50 percent. The ratio response used to be only one percent. (...) In his last year said he earned $ 480,000. Rationalize their actions to spam thinking is different than robbing people. He also discovered that many of those who bought medical products were addicted to drugs, and that the products used to be fake, imitation, adulterated versions of the originals. The Viagra was "cut" with amphetamines, other "magic pills" were manufactured in laboratories in China, India and Fiji (...) "In ten years we will still be receiving spam."
The creature has now written a book telling his story and how it is to spam techniques for better: Inside the spam cartel: trade secrets from the dark side . now available at Amazon.

The future and the spammer
Not many know but one thing that gives more money in this country but are hard to believe email marketing campaigns .. Income earned are above normal salary of any player in the first division.
First of all I would like to give you a brief definition of what is email marketing .. under concepts sought by the network:
Email marketing: is a form of direct marketing that uses email as a means of advertising or communication of messages to a specific audience.
Email marketing: are the actions and strategies for marketing through the Internet, which are carried out using the e-mail messages.
Email marketing: could be defined as the use of email for commercial purposes so that by sending emails to your customers or prospects can keep you informed about your products or services and initiate a dialogue in two directions (business - customer or prospect and vice versa).
guess I'm clear, this is an issue that attracts me MUUCHOO, however this post is not to speak especially of email marketing .. And publishes a new article on this subject. The root of this post is to let them see a bit where you get that causes brings the practice of email marketing when he became SPAM (junk mail) ..
Well here I bring a couple of news .. (Nothing new) but worth seeing .. BY OUR RETINA
I was looking for information on spam, programs, laws, etc etc. ..
And I have found especially with these 2 that UFF .. Sometimes I get to find the article and read it again and again and again! hehe .. Until this I have said baah share it with someone and then have the ad in house = P hehe ..
Here I bring you:
Sentenced to nine years in prison on eight "spammer" world's most prolific
Jeremy Jaynes, 30, has become the first spammer to be convicted U.S. to send up to 10 million unsolicited messages ("spam") that is pornographic and fake products to day. Jaynes, known as the eighth "spammer" world's busiest, has been sentenced to nine years in prison.
Judge Thomas Horne, however, delayed the Jaynes imprisonment pending an appeal, arguing that the legislation violated the detainee is new and raises several constitutional issues.
Jaynes was considered at the time of his arrest as one of the ten most responsible for sending "spam" in the world, cluttering the mailboxes of users with over ten million messages pornographic products false day. Jaynes used the pseudonym "Gaven Stubberfield" to commit their scams. In their messages, from appliances were advertised for penis enlargement to software intended to erase the trail leaves the user to browse the web.
The defendant was convicted in November of using Internet addresses and aliases to send through a Virginia-based server messages, he reported, according to the indictment, about $ 750,000 a month. Virginia law does not consider itself a crime in sending unsolicited messages over the Internet, but worth using false names for transmission. Jaynes' attorney, David Oblon, announced it would appeal the sentence on the grounds that the defendant was convicted in a state that does not reside and where legislation has been handled had entered into force just weeks before charges were filed against him.confesses A retired spammer tactics of the dark world of garbage
"I know I'm going to hell" is the owner of a great interview with ComputerWorld Australia where a spammer "retired" (not in the sense bladerunneriano , but in the economic) and some of their tactics and how the daily lives of those who send spam from the dark side. These are some of the highlights of the interview, complete worth reading:
Ed is a retired spammer made a considerable fortune sending promotional mailings pills, porn and casinos. At its peak earning between 10,000 and 15,000 dollars a week (...) He started his business when he was expelled from school at 17, until he retired at 22. "Yes, I know I'm going to hell. But I'm not bad guy, really. I'm basically everything that people hate to Internet. "
Among their techniques were sending spam to recovering gambling addicts by encouraging them to visit sites and casino games. He used the addresses of people I knew who bought antianxiety medication or antidepressants and pharmaceutical spam sent them (...) He spent ten hours a day, seven days a week studying how to send more spam and security filters overcome. "The best was sending spam, the more money earned." (...)
If someone who received the messages bought something, Ed received a percentage. In pharmaceuticals, about 50 percent. The ratio response used to be only one percent. (...) In his last year said he earned $ 480,000. Rationalize their actions to spam thinking is different than robbing people. He also discovered that many of those who bought medical products were addicted to drugs, and that the products used to be fake, imitation, adulterated versions of the originals. The Viagra was "cut" with amphetamines, other "magic pills" were manufactured in laboratories in China, India and Fiji (...) "In ten years we will still be receiving spam."
The creature has now written a book telling his story and how it is to spam techniques for better: Inside the spam cartel: trade secrets from the dark side . now available at Amazon.
Will A Universal Remote Work On A Dvd Recorder?
Jump captcha www.megaupload.com By Hielasangre
Create a database (emails)
As we all know to get email 's by spiders does not work, most of the email's that we have obtained will be foreigners, invalid, inactive, etc.
I assure you that with this type of work the results are expected. Quietly
can get 20,000 emails in less than 10 minutes, and of course, all valid and current. For Email Marketing or for the use that you please give.
PROGRAMS NEEDED:
Windows Mails
eMail Extractor Extension Changer
STEP 1: logger with an employed (each as you can get it)
STEP 2: Remove obsolete mails (facebook, promos, etc)
OPTIONAL: delete messages with attachments to accelerate
STEP 3: Download to PC mails
STEP 4: Change the extension files obtained.
TXT STEP 5: Use the exhaust mails to get a new mailing list without duplicates.
OPTIONAL: from excel you can use the utility to remove auto filter emails with specific domain (. .gob-.mil Education, "etc.)
READY! is very common for doing this once and obtain a list of about 20 000 unique emails.
Knowing that we are getting emails has something to prove is to place the same account as the sender, and thus try to skip a bit anti-spam filters in Hotmail
leave the video below where I just explained above from beginning to end so that they better understand each step.
Download video (high quality):
Emailing.rar Get emails for
Programs used: eMail
Extractor.rar
File Extension Changer.rar
Video Online (low quality):
http://www.megavideo.com/?v=RS7PMET3 
Create a database (emails)
As we all know to get email 's by spiders does not work, most of the email's that we have obtained will be foreigners, invalid, inactive, etc.
I assure you that with this type of work the results are expected. Quietly
can get 20,000 emails in less than 10 minutes, and of course, all valid and current. For Email Marketing or for the use that you please give.
PROGRAMS NEEDED:
Windows Mails
eMail Extractor Extension Changer
STEP 1: logger with an employed (each as you can get it)
STEP 2: Remove obsolete mails (facebook, promos, etc)
OPTIONAL: delete messages with attachments to accelerate
STEP 3: Download to PC mails
STEP 4: Change the extension files obtained.
TXT STEP 5: Use the exhaust mails to get a new mailing list without duplicates.
OPTIONAL: from excel you can use the utility to remove auto filter emails with specific domain (. .gob-.mil Education, "etc.)
READY! is very common for doing this once and obtain a list of about 20 000 unique emails.
Knowing that we are getting emails has something to prove is to place the same account as the sender, and thus try to skip a bit anti-spam filters in Hotmail
leave the video below where I just explained above from beginning to end so that they better understand each step.
Download video (high quality):
Emailing.rar Get emails for
Programs used: eMail
Extractor.rar
File Extension Changer.rar
Video Online (low quality):
http://www.megavideo.com/?v=RS7PMET3
Wednesday, April 21, 2010
Internal Deepthroat Manga
good Newbie's Guide. Murder By
Mysterious
Svchost.exe Svchost.exe is arguably the most mysterious process Windows. Svchost.exe is a name of generic host process for services that run from dynamic link libraries (DLL). The Svchost.exe file is located in the% SystemRoot% \\ System32.
At startup, Svchost.exe checks the services portion of the registry to construct a list of services to be charged. It is possible that the system multiple instances of Svchost.exe running at the same time. Each Svchost.exe session can contain a grouping of services. Therefore, it can run different services depending on how and where Svchost.exe is started.
Svchost.exe groups can be identified in the following registry key:
HKEY_LOCAL_MACHINE \\ Software \\ Microsoft \\ WindowsNT \\ CurrentVersion \\ Svchost
Some gusanos se aprovechan de este proceso para camuflarse en el sistema y no ser detectados con una simple exploración de procesos. Existe malware que utiliza esta técnica de camuflaje como los gusanos: Jeefo, Welchia, Assarm y más recientemente el Conficker.
Con la herramienta gratuita Svchost Process Analyzer podemos enumerar todos los procesos svchost del sistema y comprobar los servicios que contienen. Aunque existe una forma de comprobarlo, en la consola de comandos mediante las ordenes: “Tasklist /SVC” y “Tasklist /FI "PID eq IdDeProceso" (con las comillas)”. Se obtiene más información y más concisa con Svchost Process Analyzer.
Esta herramienta está disponible para: Windows Vista, XP, 2000 and 2003. For proper use of the svchost process analyzer, it should run as a system administrator account.
More information and download Svchost Process Analyzer:
http://www.neuber.com/free/svchost-analyzer/index.html
Description of Svchost.exe in Windows: http
: / / support.microsoft.com/kb/314056/es
Tools for virus detection and disinfection Conficker:
http://vtroger.blogspot.com/2009/04/herramientas-para-la -detection-y.html 
Mysterious
Svchost.exe Svchost.exe is arguably the most mysterious process Windows. Svchost.exe is a name of generic host process for services that run from dynamic link libraries (DLL). The Svchost.exe file is located in the% SystemRoot% \\ System32.
At startup, Svchost.exe checks the services portion of the registry to construct a list of services to be charged. It is possible that the system multiple instances of Svchost.exe running at the same time. Each Svchost.exe session can contain a grouping of services. Therefore, it can run different services depending on how and where Svchost.exe is started.
Svchost.exe groups can be identified in the following registry key:
HKEY_LOCAL_MACHINE \\ Software \\ Microsoft \\ WindowsNT \\ CurrentVersion \\ Svchost
Some gusanos se aprovechan de este proceso para camuflarse en el sistema y no ser detectados con una simple exploración de procesos. Existe malware que utiliza esta técnica de camuflaje como los gusanos: Jeefo, Welchia, Assarm y más recientemente el Conficker.
Con la herramienta gratuita Svchost Process Analyzer podemos enumerar todos los procesos svchost del sistema y comprobar los servicios que contienen. Aunque existe una forma de comprobarlo, en la consola de comandos mediante las ordenes: “Tasklist /SVC” y “Tasklist /FI "PID eq IdDeProceso" (con las comillas)”. Se obtiene más información y más concisa con Svchost Process Analyzer.
Esta herramienta está disponible para: Windows Vista, XP, 2000 and 2003. For proper use of the svchost process analyzer, it should run as a system administrator account.
More information and download Svchost Process Analyzer:
http://www.neuber.com/free/svchost-analyzer/index.html
Description of Svchost.exe in Windows: http
: / / support.microsoft.com/kb/314056/es
Tools for virus detection and disinfection Conficker:
http://vtroger.blogspot.com/2009/04/herramientas-para-la -detection-y.html
White On White Silverado
Social Engineering, Cash with CC's and Paypal. By Puzzle
Googlebot vs your web
Looking Websites, and all that, I found this article pretty cool haha, I mean, to see if .. Are to index or something:) haha \u200b\u200b.. So good here I leave the code:

Googlebot vs your web
Looking Websites, and all that, I found this article pretty cool haha, I mean, to see if .. Are to index or something:) haha \u200b\u200b.. So good here I leave the code:
\u0026lt;?
php if (strpos ($ _SERVER ['HTTP_USER_AGENT'], 'Googlebot')! == False) {
/ / Tu Email
direccecion
$ email_address = 'tu@tudominio.com';
/ /
Instead, send the email mail ($ email_address, 'Googlebot Alert',
'The Googlebot has visited your site: '. $ _SERVER [' REQUEST_URI ']);
?>
Snl Jay Mohr Christopher Walken
Social Engineering & Paypal. By Puzzle
eliminates the time-out (megaupload)
Reading around I saw there was a way to skip the captcha mega, so I made a script in php, as usual: P
The only thing the script does is add to our following url "mgr_dl.php? d =" to manage the download automatically.

eliminates the time-out (megaupload)
Reading around I saw there was a way to skip the captcha mega, so I made a script in php, as usual: P
The only thing the script does is add to our following url "mgr_dl.php? d =" to manage the download automatically.
\u0026lt;style>
body, a, a: link, a: visited, a: hover, td {
font-family: verdana, sans-serif;
font-size: 16pt;
color: black;
}
a { font-weight: bold; }
input {
font-family: verdana, sans-serif;
font-size: 16pt;
border: black 2px solid;
padding: 2px;
}
#vid {
width: 500px;
}
</style>
<center>
<title>MegaDownloader - RemoteExecution</title>
<img src="http://img252.imageshack.us/img252/1215/mick.jpg"><br>
<form name = "pr" action = "" method = "post">
align="center"> \u0026lt;table
\u0026lt;td> \u0026lt;input id = "button" type = "text" name = " web "size =" 50 "maxlength =" 110 "value =" \u0026lt;? php echo $ site; ?>">\u0026lt;/ td>
\u0026lt;td> \u0026lt;/ td>
\u0026lt;td> ; \u0026lt;input type="submit" name="submit" id="boton" value="Descargar"> \u0026lt;/ td>
\u0026lt;/ table>
\u0026lt;/ center>
\u0026lt;?
php ini_set ('user_agent', 'Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US, rv: 1.8.1.9) Gecko/20071025 Firefox/2.0.0.9');
/ ** * @ author
www.delincuentedigital.com.ar
* @ copyright
16/11/2009
* /
$ web = $ _POST ['web'];
$ submit = $ _POST [ 'submit'];
$ search = 'http://';
if (isset ($ web web )&&($! = "")&&( isset ($ submit) & & ($ submit! = "")))
{/ / test url:
http://www.megaupload.com/?d=TADMUPNB
if (ereg ($ search, $ web)) {
} else {$ web = $ find. $ web;}
$
url_divida = explode ('? d =', $ web);
$ url_generada = $ url_divida [0]. "mgr_dl.php? d = '. $ url_divida [1];
echo' \u0026lt;iframe src ="'.$ url_generada. '"
width =" 0 "height =" 0 "scrolling =" auto "frameborder =" 0 "transparency>';}
?>
Saturday, April 17, 2010
Pinball Harmem Globe Trotters
little hack Guide
Preface: Everyone
newbies, some in this, others in this. If you know you behave, you adapt to the rules "unwritten" and not too annoying, you're probably well received and accepted.
The intention of this paper is to help newcomers in Computer Security (come on, hacking ), to take his first steps without disengage. I write because I've seen a lot of new people and I think I need a text like this. Finally I
important to note that when I refer (below) to "we", I will be doing to all those who communicate with the ideals that arise. Regardless level or seniority.
Paragraph One: The rules and customs.
"When in Rome, do as the Romans do" and that in any social group is a set of standards that should be met if you want to be accepted. This is rather a lot, I will simply refer as an example a few and invite the reader to investigate (which happens to be one of the most important standards) for himself.
questions, including: Do not think you're so bad, not that we do not like to help ... is that your questions are rather vague, leaving us no alternative but to send you to google. Before asking any questions on any topic, make sure of never having spent half an hour searching and informing about your question.
This is a very important point, the questioner usually ends with a stamp that says " LAMM " on the forehead and going to be ignored forever.
trusts with your friends: And is that nobody likes to be added to MSN to enter as "What we fart" followed by "Hey wimp, I do a fabor ?."
If you go to add someone to msn , you should consult it before in some other way if you care. And if you're going to ask someone for help, do with respect and courtesy.
Spelling, at least: not that we are all lit from the literature and the arts. Is that when something is hard to read, for it is written, the content loses interest.
Try to speak and write correctly, the way you talk and write is your only letter.
not pretend to learn the method without knowing the theory: And is that today the question I'm most asked is "How Defacer" or "As spamming" and all that irritates me, if you do not know a command * nix , how you intend to change the index ? Ah, yes, now there shells with small buttons ... Well, if you're such, do not talk to me.
Knowledge, common goal: For that reason, look no show that you know, seeks to learn. A deface my sister can do it face down, hands tied and blindfolded ... Yes! Do not ask how.
here all seek knowledge and each individual is worth exactly as much as you know.
Paragraph Two: The essential and recommended.
He who knows not and knows not that he does not know, is a fool. Avoided.
The first step to learn is to know / want to learn and know what to learn. This may sound redundant and even obvious, but many people want to learn to "be hacker "Without really knowing what being a hacker and what knowledge one.
on knowing how to learn, say, that not enough to know something practical approach, the theory is absolutely essential to understand. Your goal should not be able to do, but know-how.
To learn I recommend you look for a suitable text, I read and reread, google all your questions and broaden much information as possible, then you practice and get back to practice, be sure to inform you of why each thing and do not stop thinking about "how it works" every thing.
on what to learn, this is much more complicated and comprehensive. The good news is that you can go little by little, only need to know where to start.
I would say the first step you should take is to learn to use Linux like Windows " natively." You should know that the Internet works on * nix , so it is very important that you move comfortably through a console, you understand the system directories, you know they do set up Internet services (web server, ftp, etc).
The second step is learning to program, the first language is a sensitive issue, I think the first thing you need is knowing how to program scripts . For this and you're at linux, I would recommend learning Bash, scripting language most unixes . Then you have to learn programming languages \u200b\u200b web undoubtedly be the first PHP.
Some here say, "But I want to hack I do not want to be a programmer or system administrator!", Well ... hack is that you know more security programmer and administrator: P
Section Three: General recommendations
* Choose a nick original and not change it. Please note that all will know you by your nick , If you choose a nick as Haxor "will be one more than himself" Haxor . " The nick is something that does not change, when people know you by your nick not force them to learn another.
also prevents things like leet speak , references to hacking and obscenity.
* If all you want is to "delete web pages " better let ... or reward yourself and now. But do not think a blog to show the world your accomplishments, not interested.
* Another recommendation is to keep a low profile, even when you consider you know better than the rest of the people I talked.
* If you do not know, do not pretend to teach. Often newbies precedence to collaborate with the community to their own learning, it hurts the player and themselves. The first step is learning to collaborate, learn and do compulsively.
* Never try to appear more educated than they really are. Even if you think you can fool us, the sooner you catch a liar than a lame. There is nothing worse than a newbie hacker pretending to be a Lammer.
* Be careful with your teachers, choose a bad teacher can make you in a bad pupil. Do not deify anyone, the gods on Mount Olympus, we're all human, we all have flaws. It is critical to judging people, especially if you intend to teach.
* Read everything you can, even more. Any topic that interests you is good reason to start learning. Here you will find many interesting articles that entertain you:)
Paragraph four: Recommended reading.
When I started in computer security that Google did not exist, information is lost in a yahoo that left much to be desired and hundreds of pages with garbage webs. Now is possible due to serious seekers and communities, find lots of articles highly recommended to read.
I'll just recommend some texts for beginners , I've read and I found an excellent start and first step.
Farewell: You've taken the first step.
If you've gotten this far, you've taken the first step in your long journey. Many will say, "this is not for me" and I'm glad. Those who stay, welcome.
If you want to include something in the text, consider leave without mentioning some important aspect or a correction like me, leave a comment.
article Originally written by Lisandro Lezaeta "Murder "
Pain In Jaw And Ear When Drinking Alcohol
Paypal Vs Social Engineering (2)
PROLOGUE:
This section will talk a bit of a technique that helped me and COST OO hehe to get a little with cash to the cc's and paypal. In the previous article explains a method of us with a Paypal account linked with another person using a little social engineering, this method works best with cc's (get every one of you as best you know;)
TOOLS:
_
Electronic Music _
Having studied some methods of payment and security / requirements at the time of paying and receiving of different online poker sites
_ A cyber-cafe far from home
_ A couple of balls
PART 1:
brief explanation, what we do is to load 2 accounts at some poker online .. One with his own money and the other with money from one of our acquisitions, cc's or paypal (We recommend using an accomplice to this method!! At least it is MUCH more comfortable and less suspicious)
In the first account (created by your partner) must deposit money in our pockets for a prepaid method (ukash, paysafecard, etc) No need to load the account with 500 euros .. 20 euros to put him enough. This account should put the actual data of the person in this case (I recommend an accomplice) So not figured anywhere! O) We take care of our asses. They say that prison does not have Vaseline! (We do not find out) ^ ^
In the second account (created for you and a cyber-cafe) deposit money from paypal cc's or any of our victims!
Note1: You need to test some "MANY" poker pages before doing this, not all can deposit money, have verifed by visa (for example) and methods have to look COBRA, because if the mess is much there is a 80% chance that no one managed to get hard to that account.
Once we have created both accounts move to the next step
PART 2:
At this point we're going to confuse a little, (is needed). I'm talking about messing around with other people who have nothing to do, lose a bit different, gain a bit different, we'll do a bit of "history play" (As in every page there are moderators, if you see a strange move given BAN )
Note2: Everything written in this section is not an "IDEA" are results! Experiments made by me that I take more than a couple of months to achieve understanding The operation of these pages!
When we have some history in our accounts, it's time to make the transfer. I call this "WASH VIRTUAL MONEY ^ ^", play with our accomplice and leave all our money to win (PLEASE do so in a credible way) nothing and leave the game begins! I remind you .. HAVE GIVEN ME BAN MUUUUUUCHOS before you can make money from this method .. At the end I will post some technical advice.
The reliability of this method is only in you! THE way despistáis technical team page ..
The idea is to spend a reasonable amount of money "not high" on account of our accomplice, Once done, the sooner claim this money, "WON"
Note3: This method is not 100% sure, for a thousand reasons .. Here I will post some tips to not charge duréis months in your first pay as happened to me>. <>. < ) Recordar que nuestra cuenta LEGAL no debe correr peligro (somos un jugador mas en esta pagina) “entre mas ofendido estés, menos sospechoso pareces” _ Entre tantos consejos, solo puedo decir que si intentáis este método y tenéis alguna duda, escribirme un pm con gusto puedo contestar las interrogantes CONCLUSION:
This method was discovered by me, VAMOS bone was not discovered that many more people I guess it has. . Trying to say that was the result of my trials and research in a desperate attempt to make easy money = D
If you know how to do, I promise you easy money .. I tried it with paypal and cc's. . and 60% of my tests were with paypal and cc's of relatives and acquaintances ^ ^ CLEAR by muyyyy little money, so I realized was how this system works!
I hope you liked it and if you practice some day, leave it in your poker accounts money a bit different so we let a couple of games .. lol
"Where Mitnick would have come without social engineering?" Greetings fellow
.. PUZZLE by
What Kind Of Cheese Do They Use A East Sides
Paypal Vs Social Engineering (1)
PROLOGUE:
This section will explain a bit what my experience has led me to know and do.
Using a bit of social engineering will link the bank account of another person to a paypal account set up for us! Easy? SI. Useful? Maybe!
What will here be considered that readers have a minimum of knowledge to some terms!
do not intend to earn the title of "best" or anything, on the other hand if one has been involved in such "illegal acts" will be my best friend! And you can be bothered to discuss. .!
TOOLS:
_ _ An electronic music out eyebrows, a fork (or anything else that serves to draw cards in a mailbox outside)
_ A cyber-cafe far from home and where did you get that letter
_ A couple of balls
PART 1:
Some may already imagine what we will.
And congratulations to those analysts, basically what we need to be: The bank account of a person, his full name, postal code. VAMOS anything that is not in a bank statement sent to house, 0)
(To register a paypal account, we ask our bank account number, Paypal us a couple of tanks which serve to verify our account within 2-3 days.)
Our mission? Register a paypal account with another bank! Let
a mailbox! (Remember the place where you get to the mailboxes), I recommend making several attacks (40% of cases, people notice of our intent to scam and cancel all exit and entry by paypal to your bank!) and please do not do this in your own building = S I speak from experience OWN! It is much more comfortable but then get what you pay! ¡¡¡¡¡¡¡¡¡¡¡¡¡¡¡ AND I AM NOT RESPONSIBLE FOR YOUR USE OF THIS INFORMATION DEN !!!!!!!!!!!!!!!!!
We take an extract, we link a paypal account with this data: bank account name, zip code, address! (Remember to make a unique email for this task)
recommend at this stage of the process, take notes, a notebook with addresses where you have taken extracts from the email account associated with each of the pass, the date of registration account .. (All this should burn once we have achieved our goal )!!!!
also worth mentioning that the hard work starts after the first day, ie the second day after our discomfort. . We go through every mailbox where we registered the accounts, since in these extracts will find the treasure we seek (THE AMOUNT THAT PAYPAL HAS DONE TO THIS PERSON TO BE ABLE TO REGISTER us)
SOME
TIPS:
_ Never let yourself be seen by anyone when messaging STEAL a third party (and if that happens, abandon the mission to that victim)
_ E (in Spain at least) shared at noon, but pulling in the morning .. 80% of people who work and earn money honorably, come early and come to their homes beginning the evening!
PS: THE BEST TIME to do this, it would be between 13:00 and 15:00 hours. NOVATO
_ If any doubt! And he is an adult .. PLEASE ASK before .. Could go straight to prison, and we are talking about 6 + years (and remember, do not have a social class division in jail, ie I locked up with Charles Manson, 0)
PART 2:
Anyone who managed to register a foreign bank account in paypal will give you a CONGRATULATIONS ..
However, this is the least fun =) Since paypal has a kind of insurance that we buy what we buy but the account holder is willing to return all payments have been made to these accounts ..
Here again have to be smart! And choosing well the places and things that caught!
Speaking from my experience: With this method I caught a million things and only very few I have been in my possession!
who thought he could pinch a lifetime megaupload account EG .. You can stop dreaming! Not last more than 5 days. .
Among the many experiments one of the methods that but I have worked and why I like to wash the money .. Is to buy virtual money in a role-playing game .. and then resell it at half price!
PS: If any of you use this method in his experiments and more black holes note hehe POST does not?
CONCLUSION:
I'd leave some screen some of my achievements, but only achieving my goal BURNS ALL and try not to leave any evidence and even some I should stay not the postearía = D hehehe. .
Remember we're talking about link the bank account of another person with a paypal account that we will use .. IE .. To give an example: Once I get over 3mil euros of one of these accounts = S and give you an idea!
In the next article I will talk about credit cards and how to take CASH.
Greetings colleagues,
by PUZZLE.
Subscribe to:
Posts (Atom)